C-Days 2024 - CSCPT CTF
Table of contents#
| Challenge | Category | Points |
|---|---|---|
| Notepad | Forensics | 150 |
| OpenSSL | Forensics | 285 |
| Billionaire’s Game | crypto | 285 |
Write-up#
Forensics#
Notepad#
Pretende-se saber a data e hora da penúltima execução do binário notepad.exe no sistema WRK01. Para o efeito são disponibilizados um conjunto de artefactos.
A flag tem o formato CSCPT{YYYY-MM-DD HH:MM:SS} com a data e hora da penúltima execução do notepad.exe.
There was an attached archive with the forensic artifacts from the WRK01 system:
[morim@sucurilabs notepad]$ ll
total 12M
drwxr-xr-x 19 morim morim 4.0K Apr 27 21:06 WRK01-KANSA
-rw-r--r-- 1 morim morim 12M Jun 18 16:03 WRK01-KANSA.tar.gz
[morim@sucurilabs notepad]$ ll WRK01-KANSA
total 84K
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:20 Arp
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:06 DNSCache
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:06 Handle
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:19 LocalAdmins
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:20 NetIPInterfaces
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:20 NetRoutes
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:20 Netstat
drwxr-xr-x 2 morim morim 20K Jun 18 16:06 PrefetchFiles
drwxr-xr-x 2 morim morim 4.0K Apr 28 00:37 PrefetchListing
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:06 SmbSession
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:06 SvcAll
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:21 SvcFail
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:19 SvcTrigs
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:19 Tasklistv
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:18 WMIEvtConsumer
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:18 WMIEvtFilter
drwxr-xr-x 2 morim morim 4.0K Apr 27 21:18 WMIFltConBind
[morim@sucurilabs notepad]$
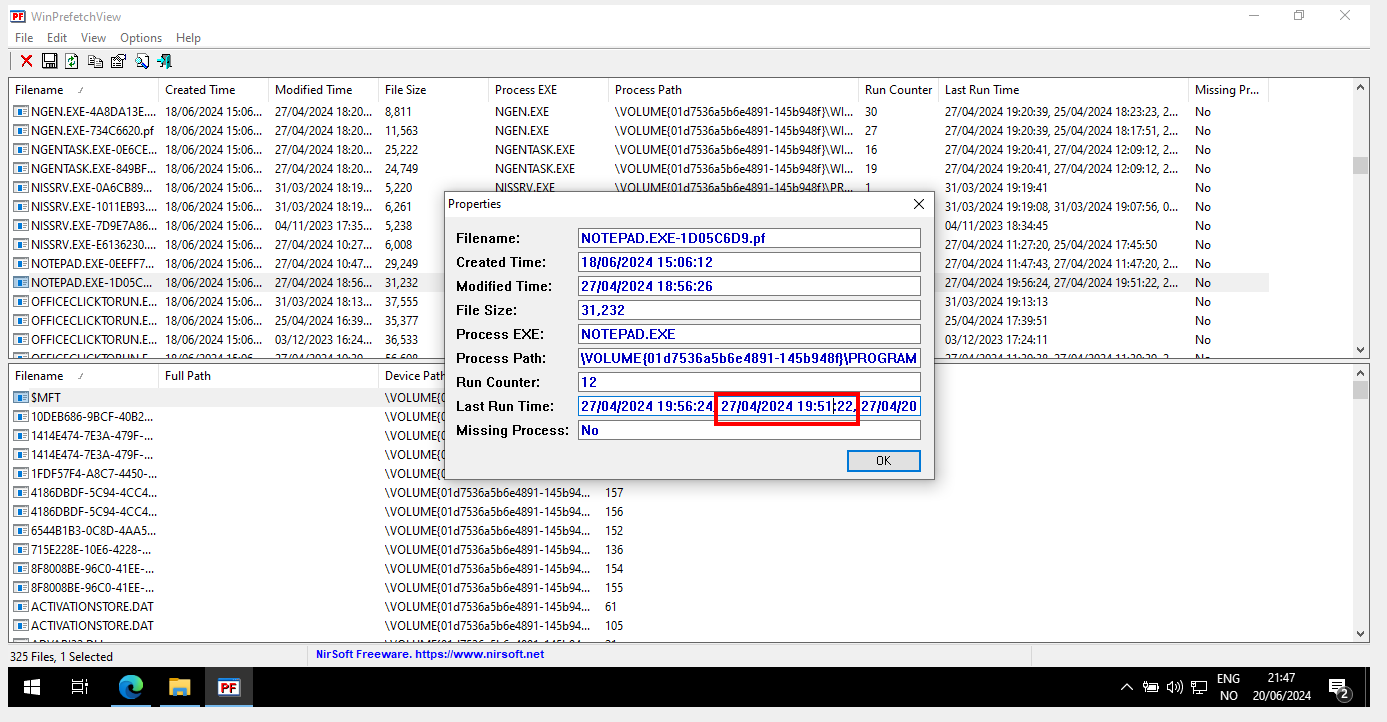
Right away we can notice that there are some PrefetchFiles which we can use to get the second to last execution time of notepad.exe.
To do that we’ll use WinPrefetchView from Nirsoft, load these prefetch
artifacts and search for the second to last execution time:
OpenSSL#
Suspeita-se que um utilizador tenha feito upload de um ficheiro sensível para a Internet.
Dispomos de uma captura de rede (eth1.pcapng) bem como de uma captura de uma cópia para um dispositivo USB (usbmon2.pcapng).
Será que conseguimos encontrar a flag?
For this challenge we are provided with a archive containing a network capture and
a USB capture. So right of the bat we are going to fire up wireshark to inspect the
traffic:
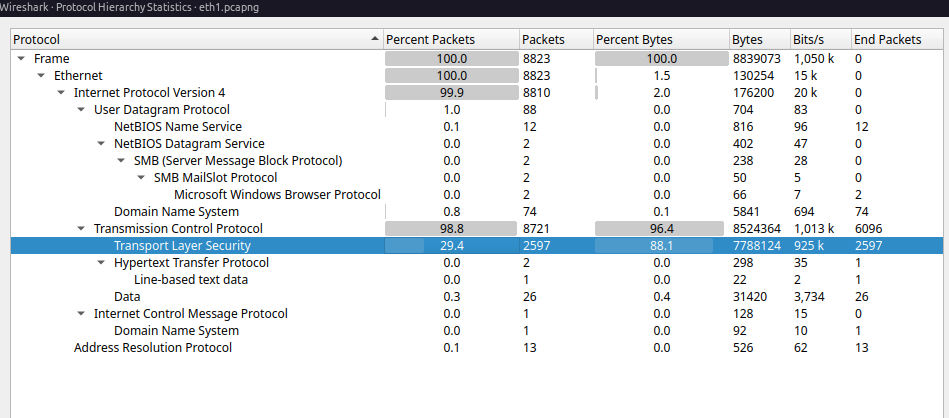
By looking at protocol hierarchy we can assume that without decryption of the tls protected data its unsolvable. Let’s check the usb capture and hope we find something that can help us continue:
[morim@sucurilabs openssl]$ binwalk -q -e usbmon2.pcapng
[morim@sucurilabs openssl]$ head -n2 _usbmon2.pcapng.extracted/soooosecretttttt.txt
CLIENT_HANDSHAKE_TRAFFIC_SECRET 8d496e73d7d62fd4d17feb2a36eb8611e40fc6ce05b437fdf5c764b6218d8b27 4a1f85ede6f03d061c017b6909f88f4fb8106c42891f064011b0a437a1a3480f
SERVER_HANDSHAKE_TRAFFIC_SECRET 8d496e73d7d62fd4d17feb2a36eb8611e40fc6ce05b437fdf5c764b6218d8b27 164993b00e19744f30f3cf500f19c5538872b96f753f8122c661e254708cdc34
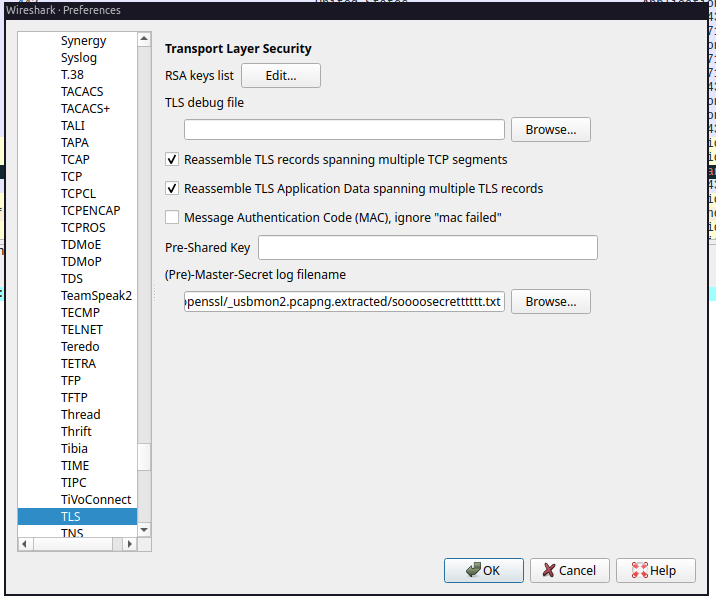
With the help of binwalk we were able to extract a text file containing the TLS
secrets for decryption of the network dump. Now it’s just a matter of loading this file
onto wireshark and continue to search for the flag:
Now that the traffic is searchable we can export all the HTTP objects since we are searching
for a uploaded file and most of the traffic is HTTP:
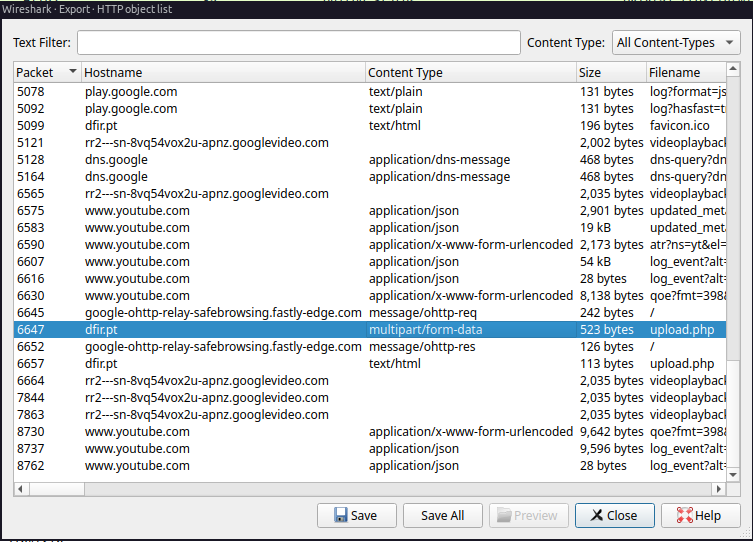
After we need to use binwalk once again to extract the file in the exported HTTP object:
[morim@sucurilabs openssl]$ binwalk -e upload.php
[morim@sucurilabs openssl]$ ll _upload.php.extracted/
total 8.0K
-rw-r--r-- 1 morim morim 359 Jun 18 17:46 A4.zip
-rw-r--r-- 1 morim morim 96 May 22 21:16 secret.enc
[morim@sucurilabs openssl]$
Looks like we have an encrypted file but we can find the encryption key in the
network capture by investigating all the traffic with the domain to where the file was
uploaded:
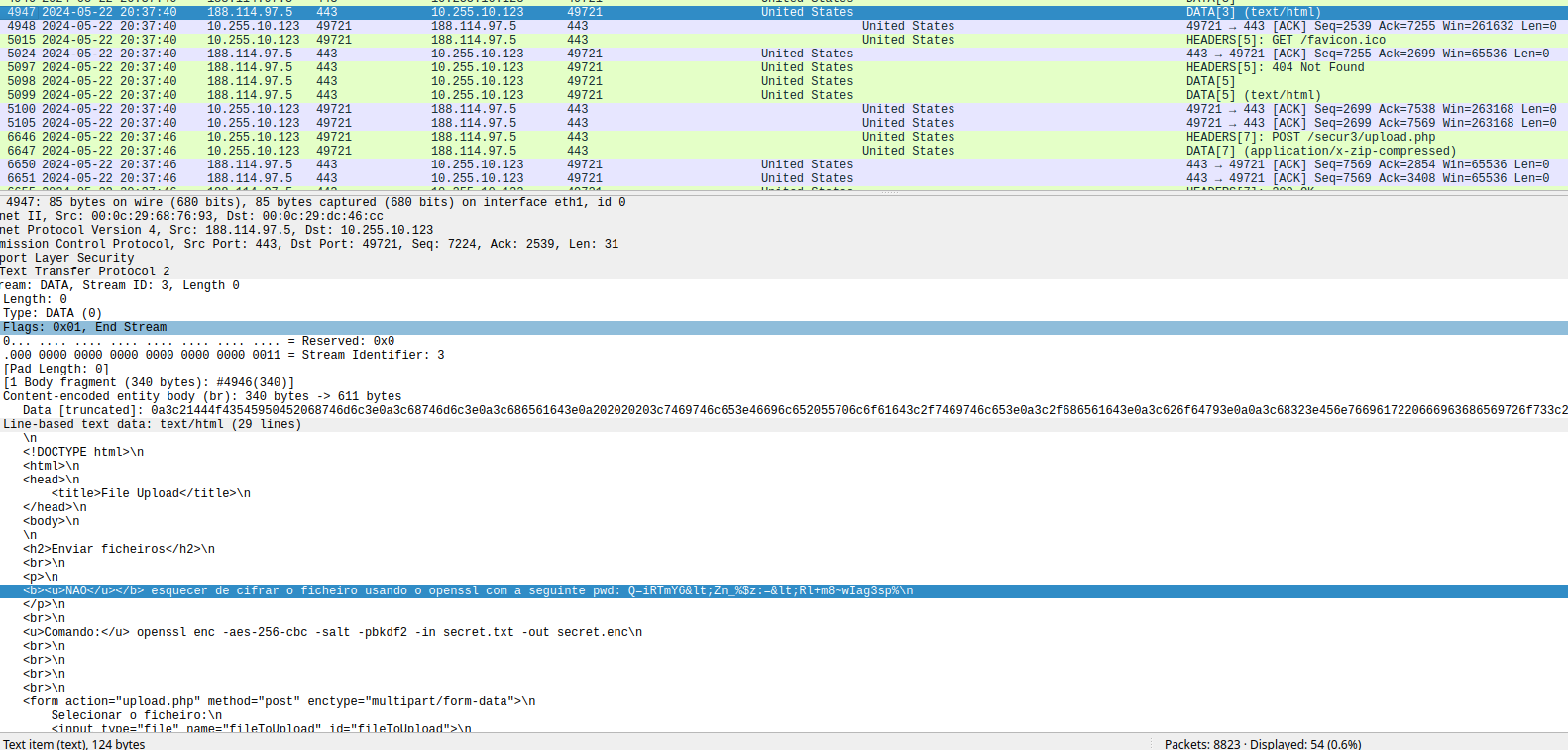
[morim@sucurilabs openssl]$ openssl enc -aes-256-cbc -salt -pbkdf2 -in _upload.php.extracted/secret.enc -d
enter AES-256-CBC decryption password:
CSCPT{8d9130825570c6d90a3e8b0ea171b8ffcbf5d26ce1dbf709e907066766673a5c}
Crypto#
Billionaire’s Game#
We are launching this new crypto currency that is so great that we even let you play with an advantage.
Can you become a billionaire?
This challenge was solved with an unintended solution. While playing the game I noticed that the wallet and the signature state where handled by the client. We can abuse this to solve the challenge by only updating the state when a bet is won and never update it when a bet is loss. By doing this we can reach to the required wallet value with ease and get the flag:
from pwn import *
import time
import json
def get_wallet(p):
p.recvuntil(b"Here is your wallet: ")
wallet = p.recvline().strip()
log.info(f"Wallet: {wallet}")
w = json.loads(wallet.decode())
return w
def get_sig(p):
p.recvuntil(b"Here is the signature: ")
sig = p.recvline().strip()
log.info(f"Sig: {sig}")
return sig
#p = process(["python", "Downloads/billionaires.py"])
p = remote("game.cybersecuritychallenge.pt", 24301)
p.recvuntil(b"What is your name?")
p.clean()
p.sendline(b"A")
lost = False
wallet = None
sig = None
while True:
if not lost:
wallet = get_wallet(p)
sig = get_sig(p)
p.recvuntil(b">>> ")
if wallet['value'] < 1000000000:
p.sendline(b"1")
p.sendline(json.dumps(wallet).encode())
p.recvuntil(b">>> ")
p.clean()
p.sendline(sig)
p.recvuntil(b">>> ")
p.clean()
p.sendline(str((wallet["value"]-5)))
p.recvline()
status = p.recvline().strip().decode()
lost = status == "You lost"
else:
p.clean()
p.sendline(b"2")
p.recvuntil(b">>> ")
p.sendline(json.dumps(wallet).encode())
p.recvuntil(b">>> ")
p.clean()
p.sendline(sig)
print(p.recv())
break
[morim@sucurilabs billionare]$ python exp.py
[+] Opening connection to game.cybersecuritychallenge.pt on port 24301: Done
[*] Wallet: b'{"value": 100000, "player": "A"}'
[*] Sig: b'0zVutpH63+7pFfAEDZilDLrJdi7KEp8z+tbD1kIDmelWwmM+YLrUG/zUKpgxNN+4'
[*] Wallet: b'{"value": 199995, "player": "A"}'
[*] Sig: b'+uc/dcf/NyFPRluOUNINYbrJdi7KEp8z+tbD1kIDmelWwmM+YLrUG/zUKpgxNN+4'
[*] Wallet: b'{"value": 399985, "player": "A"}'
[*] Sig: b'MojUPtI8KJdSbmGwek6WuLrJdi7KEp8z+tbD1kIDmelWwmM+YLrUG/zUKpgxNN+4'
[*] Wallet: b'{"value": 799965, "player": "A"}'
[*] Sig: b'y9IPG+sHq02VKpnfXWrGerrJdi7KEp8z+tbD1kIDmelWwmM+YLrUG/zUKpgxNN+4'
[*] Wallet: b'{"value": 1599925, "player": "A"}'
[*] Sig: b'txjajyTyI2Gknww2+Y6nKbYAJwWMR2/+Wo9O/GfcEk8tUAQyio/tLhS++zlQ9VQm'
[*] Wallet: b'{"value": 3199845, "player": "A"}'
[*] Sig: b'EIRpEYex+dHPgvfWXVHOy7YAJwWMR2/+Wo9O/GfcEk8tUAQyio/tLhS++zlQ9VQm'
[*] Wallet: b'{"value": 6399685, "player": "A"}'
[*] Sig: b'PPtM+r9LdPhlt4tNpPAArLYAJwWMR2/+Wo9O/GfcEk8tUAQyio/tLhS++zlQ9VQm'
[*] Wallet: b'{"value": 12799365, "player": "A"}'
[*] Sig: b'wlX+5C4ZQ+pRLQP8GXtn282/IPPtdbBC1kAAAQNU7yiillYWJSQXe9az6nppyQro'
[*] Wallet: b'{"value": 25598725, "player": "A"}'
[*] Sig: b'3JTIxgVOXfCLUOk0RVjGqTMDfEFJSvnJ4kd1Ny+HfMGillYWJSQXe9az6nppyQro'
[*] Wallet: b'{"value": 51197445, "player": "A"}'
[*] Sig: b'ha6pWaw0aLmJUDboMnpBuADn5qDS4AOouNbtJwDwAm6illYWJSQXe9az6nppyQro'
[*] Wallet: b'{"value": 102394885, "player": "A"}'
[*] Sig: b'TMuDmylNqg9zJECi6yQMQ0w3iGuMW4j0RhKnVt927CgsQS5oDmPnTTSGL9CvVvoa'
[*] Wallet: b'{"value": 204789765, "player": "A"}'
[*] Sig: b's7YktwmLCZNuWj/eOUZOPr8YB2BtmQ9G9cMsgb7/35wsQS5oDmPnTTSGL9CvVvoa'
[*] Wallet: b'{"value": 409579525, "player": "A"}'
[*] Sig: b'E/qO/W0NGCDuf6cDumKHm9vUPaWXLqsvgJnUv7IXWr8sQS5oDmPnTTSGL9CvVvoa'
[*] Wallet: b'{"value": 819159045, "player": "A"}'
[*] Sig: b'wG1cIA3aICGh1U6h1Tfh2KqLEDUUuFYdO+qVwd5ZYxksQS5oDmPnTTSGL9CvVvoa'
[*] Wallet: b'{"value": 1638318085, "player": "A"}'
[*] Sig: b'dj19p11MontJn/hmlMWFzdhtxtXfWbbT7aPJIWbb8ENZMMRVecJ4g+nN1eeoQwZZ'
b'Here is the flag: CSCPT{ECB_is_not_resilient_against_permutation_of_blocks}\n'
[*] Closed connection to game.cybersecuritychallenge.pt port 24301